Patching for the Meltdown vulnerability on Windows servers involves the installation of an update from Microsoft as well as making a few registry changes, and it is vital that this be done in order to protect yourselves from potential compromise. Below we have outlined a couple of different approaches to getting yourself patched.
Option 1: Our Automated Script
We have prepared scripts for the three versions of Windows Server we support that will install the required update and apply the registry changes automatically. Please note that while we are confident in this script you do use it at your own risk. The script will need to be run with Administrator privileges, and a reboot will be required for the protections to apply.
Note: we are currently seeing a substantial performance impact under Windows Server 2008 after the patch - an approximately 60% drop in disk-related performance. We are continuing to work on this in hopes of reducing this impact, but we would highly recommend upgrading to a newer version of Windows Server.
For Windows Server 2016:
https://files.sitehost.nz/meltdown/meltdown_patch_server2016.zip (1.2GB)For Windows Server 2012:
https://files.sitehost.nz/meltdown/meltdown_patch_server2012.zip (111MB)For Windows Server 2008:
https://files.sitehost.nz/meltdown/meltdown_patch_server2008.zip (67MB)
Download the required zip file for your Windows version, extract the files to a temporary directory and then run install.bat as an administrator. Remember, even with this patch installed you aren't protected until you restart your server.
Option 2: Manual Install
To install the patch, you need to manually download the patch in the links below:
Note: we are currently seeing a substantial performance impact under Windows Server 2008 after the patch - an approximately 60% drop in disk-related performance. We are continuing to work on this in hopes of reducing this impact, but we would highly recommend upgrading to a newer version of Windows Server.
Windows Server 2016:
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4056890Windows Server 2012:
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4056898Windows Server 2008:
http://www.catalog.update.microsoft.com/Search.aspx?q=KB4056897
Only download the appropriate update for the server that you are patching - e.g for Windows Server 2008 only download '2018-01 Security Only Quality Update for Windows Server 2008 R2 for x64-based Systems (KB4056897)' not the '2018-01 Security Only Quality Update for Windows Server 2008 R2 for Itanium-based Systems (KB4056897)' patch. Once downloaded, double click on the file and follow the instructions. After the installation you can delete the downloaded file as it is no longer needed.
In addition to the patch, you will need to make a few registry changes. You can do this by running the following in an Administrator-level command prompt:
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0 /f
reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 3 /f
reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization" /v MinVmVersionForCpuBasedMitigations /t REG_SZ /d "1.0" /f The server will require a reboot to apply the updates. You can either do this immediately or wait for a more convenient time, though you are not protected until you have rebooted so we recommend doing this as soon as possible.
Verifying that protections are enabled
Microsoft has provided PowerShell scripts that can be used to verify the updates installed correctly.
For Windows Server 2016
Install the PowerShell module:
PS> Install-Module SpeculationControlRun the PowerShell module to validate the protections are enabled:
PS> # Save the current execution policy so it can be reset
PS> $SaveExecutionPolicy = Get-ExecutionPolicy
PS> Set-ExecutionPolicy RemoteSigned -Scope Currentuser
PS> Import-Module SpeculationControl
PS> Get-SpeculationControlSettings
PS> # Reset the execution policy to the original state
PS> Set-ExecutionPolicy $SaveExecutionPolicy -Scope CurrentuserFor earlier OS versions (require at least PowerShell v3.0)
Install the PowerShell Module from Technet ScriptCenter:
Download SpeculationControl.zip to a local folder.
Extract the contents to a local folder, for example C:\ADV180002
Run the PowerShell module to validate the protections are enabled:
Start PowerShell, then (using the example above), copy and run the following commands:
PS> # Save the current execution policy so it can be reset
PS> $SaveExecutionPolicy = Get-ExecutionPolicy
PS> Set-ExecutionPolicy RemoteSigned -Scope Currentuser
PS> CD C:\ADV180002\SpeculationControl
PS> Import-Module .\SpeculationControl.psd1
PS> Get-SpeculationControlSettings
PS> # Reset the execution policy to the original state
PS> Set-ExecutionPolicy $SaveExecutionPolicy -Scope CurrentuserOutput
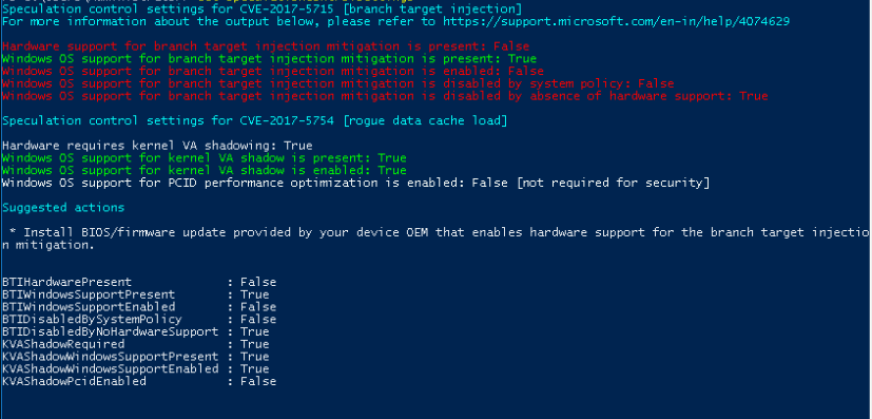
The output of this PowerShell script will resemble the following. Enabled protections appear in the output as "True."
Note that some tests are in respect to the underlying node, for which we are still waiting on the release of firmware updates. For more information on the script and its output, have a look at this article from Microsoft.